About
Information security involves protecting valuable information assets from intentional harm [57]. With the popularity of mobile and ubiquitous computing infrastructure, such as the cloud [3], the technical and social contexts in which software applications are expected to operate are increasingly dynamic. As a result, the assets, their values, and attack scenarios can easily change from one situation to another. This increases the challenge of finding out what the information assets are, who their owners are, where in the system vulnerabilities lie, and the extent to which the security requirements are satisfied. In such an environment, information security has to be highly context-sensitive: software applications must adapt to the changing contexts and respond quickly and appropriately to ensure that the requirements for information security are not violated. We call this notion Adaptive Information Security, and focus on three of its prerequisites in the context of cloud computing: (1) understanding user security requirements for cloud applications; (2) traceability between security requirements, design and implementation of some cloud services; and (3) adaptive security design for dynamic contexts.
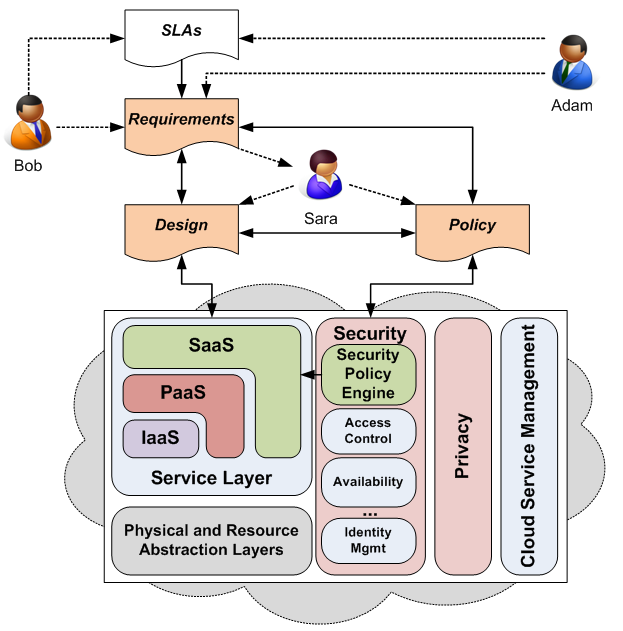
Whilst cloud computing services can adopt different models, such as Infrastructure as a Service (IaaS), Platform as a Service (PaaS) and Software as a Service (SaaS), the focus of our work is on the last of these model because this is where cloud service providers have greatest responsibility for security. The figure above shows how a user (Bob), cloud service provider (Adam) and cloud-based services developer (Sara) contribute to the security requirements, design and policies to implement the security functionality of the cloud-based software service. Here Adam and Bob provide the security requirements, either indirectly through the service level agreement (SLA) that is negotiated when Bob first signs-up for the cloud software service, or directly during the lifetime of the service. Sara, the developer, uses these requirements to derive the design of the security functionality of the cloud-based service and the policies that govern the run-time adaptation of this functionality required to handle changes in user context.
Our broad objective is to develop a tool-supported approach to elicit and relate information security requirements to design and implementation, in order that these systems are able to adapt to dynamically changing contexts whilst maintaining security. The proposed approach is based on the idea of Adaptive Information Security, and the concept, language and implementation it entails. The main aims of this collaborative project between the Open University and Qatar University are to:
- Investigate requirements modelling and analysis methods for adaptive information security by developing notations and structures for protecting assets from harm in dynamically changing contexts (A1)
- Develop techniques for design-time and run-time traceability between security design of cloud services and requirements for information security (A2)
- Develop methods for adapting and validating a system's design in the face of changing contexts and providing associated security assurance (A3)
- Implement practical mechanisms to demonstrate and validate the approach (A4)
These research aims can be refined into a number of research questions including:
- How can the notions of "anti-requirements" and "harm to assets" be used and extended when describing adaptive security requirements? (A1)
- How can requirements for adaptive information security be elicited for cloud applications? (A1)
- What kinds of traceability between static ("design time") models and dynamic (run time) models can be analysed and used to in order support security analysis and adaptation? (A2)
- To what extent can traceability from requirements to implementation be recovered? (A2)
- How can users monitor the extent to which their requirements are being satisfied as cloud services and applications evolve? (A3)
- How can developers determine the extent to which user requirements are being met by their applications? How can adaptive security requirements be enforced by security policies? (A3)
- What is the infrastructure needed for adaptive assurance mechanisms to work effectively in the cloud? What is the best way to assure users about the security of their data? (A4)
